More than 60,000 D-Link network-attached storage devices that have reached end-of-life are vulnerable to a command injection vulnerability with a…
MFA enhances the security of email accounts by requiring users to provide additional verification beyond just their password. Implementing MFA…
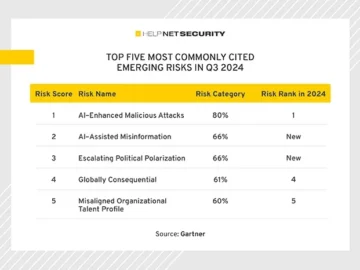
AI-enhanced malicious attacks are the top emerging risk for enterprises in the third quarter of 2024, according to Gartner. Key…
Nov 08, 2024The Hacker NewsCybersecurity Awareness / Webinar Let’s face it—traditional security training can feel as thrilling as reading the…
As more companies adopt cloud services and remote work, the limitations of virtual private networks (VPNs) are becoming obvious. VPNs…
The Canadian government has ordered TikTok Technology Canada, Inc., the Canadian arm of TikTok’s parent company ByteDance Ltd., to wind…
Palo Alto Networks warns of potential RCE in PAN-OS management interface Pierluigi Paganini November 08, 2024 Palo Alto Networks warns…
Today, cybersecurity company Palo Alto Networks warned customers to restrict access to their next-generation firewalls because of a potential remote…
Multi-stage malware means sophisticated cyberattack strategies that evolve in several steps. Recent developments in multi-stage malware highlight the increasing sophistication…
In today’s digital age, the importance of cybersecurity must be re-balanced. With increasing cyberattacks and data breaches, organizations must prioritize…
In a bold move, Apple has published a draft ballot for commentary to GitHub to shorten Transport Layer Security (TLS)…
Nov 08, 2024Ravie LakshmananCyber Espionage / Threat Intelligence High-profile entities in India have become the target of malicious campaigns orchestrated…