The Post Office is in the process of appointing a third party to review its controversial Horizon computer system amid…
State and local government and education organizations (also known as SLED) were always at risk from cyberattacks, but the rise…
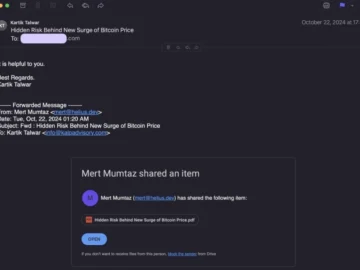
North Korean hackers are targeting cryptocurrency businesses with a sophisticated new malware campaign, dubbed “Hidden Risk.” Learn how this stealthy…
The Motley Fool reports that Tenable (NASDAQ: TENB) generated $227.1 million in revenue during the third quarter of 2024, a 13…
Over the past several years, CISA, the Cybersecurity and Infrastructure Security Agency, has released a steady stream of guidance encouraging…
A recent spear-phishing campaign targeting industrial and engineering companies in Europe was aimed at saddling victims with the popular GuLoader…
Nov 07, 2024The Hacker NewsPassword Security / Network Security Defending your organization’s security is like fortifying a castle—you need to…
The UK public is generally accepting of having datacentres built in their communities, despite research showing that large numbers of…
A significant vulnerability (CVE-2024-20445) has been discovered in Cisco Desk Phone 9800 Series, IP Phone 7800 and 8800 Series, and…
On Thursday, November 7, SonicWall is set to unveil a new security solution crafted to meet the specific needs of…
A threat actor with ties to the Democratic People’s Republic of Korea (DPRK) has been observed targeting cryptocurrency-related businesses with…
North Korean hackers are targeting crypto-related businesses with phishing emails and novel macOS-specific malware. The crypto-related phishing campaign Since July…