Public cloud storage deployments are by far the biggest storage priority for organisations in the UK and Ireland in 2023,…
A collection of mistakes that make documentation less awesome than it could be. I’ve been an editor longer than I’ve…
Apr 18, 2023Ravie LakshmananMobile Security / Hacking A new Android malware strain named Goldoson has been detected in the official…
Technology companies offering encrypted messaging services have urged the government to make urgent changes to legislation going through Parliament that…
Since secondhand equipment is discounted, it would potentially be feasible for cybercriminals to invest in purchasing used devices to mine…
Western Digital Corporation, a leading American computer drive manufacturer and data storage company, is facing the wrath of the ALPHV…
Gareth Heyes | 30 June 2021 at 16:47 UTC Of the three main types of XSS, DOM-based XSS is by…
Celebrating the accomplishments of hackers is something we want to do year-round. However, we decided we wanted to root Cyber…
Companies are finding themselves increasingly reliant on a growing number of cloud-based services, as business tools transform into online platforms,…
TL/DR: Detectify’s Hack Yourself event in Stockholm is 24 hours away, which means that it’s time to catch up on…
Cybersecurity analysts from Securonix have discovered a new malware variant hiding in the images produced by the James Webb Space…
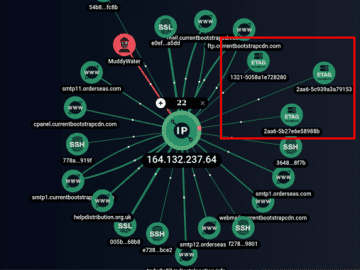
Apr 18, 2023Ravie LakshmananCyber Threat / Malware The Iranian threat actor known as MuddyWater is continuing its time-tested tradition of…