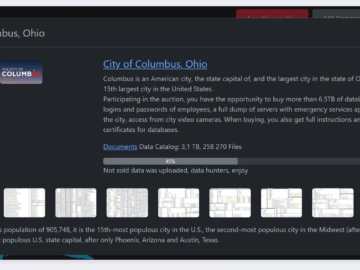
July 2024 ransomware attack on the City of Columbus impacted 500,000 people Pierluigi Paganini November 04, 2024 The July 2024…
Threat actors are abusing DocuSign’s Envelopes API to create and mass-distribute fake invoices that appear genuine, impersonating well-known brands like…
The ‘FortiJump’ vulnerability in Fortinet’s FortiManager management platform may not have been completely fixed by the company’s patch issued last…
Defence has cancelled a multi-billion dollar project for a geostationary earth orbit (GEO) satellite communications system that Lockheed Martin was…
In July 2024, the ransomware group Embargo targeted US companies using the malicious loader MDeployer and EDR killer MS4Killer. MDeployer…
Hackers claim to have breached MIT Technology Review Magazine via a third-party contractor, leaking nearly 300,000 user records on Breach…
Schneider Electric has confirmed a developer platform was breached after a threat actor claimed to steal 40GB of data from…
Researchers discovered a Russian-linked threat actor, UNC5812, utilizing a Telegram persona named “Civil Defense. ” This persona has been distributing…
We identified a new wave of phishing for banking credentials that targets consumers via Microsoft’s search engine. A Bing search…
Microsoft has announced that Windows Server 2025, the latest version of its server operating system, is generally available starting Friday,…
The “You Dun” hacking group exploited vulnerable Zhiyuan OA software using SQL injection, leveraging tools like WebLogicScan, Vulmap, and Xray…
A ransomware attack against the City of Columbus, Ohio—which drew public scrutiny following the city government’s attempt to silence a…