The seven pillars of the Department of Defense (DOD) Zero Trust Reference Architecture provide a comprehensive framework for securing today’s…
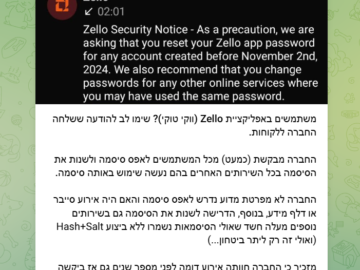
Zello urges users to reset passwords following a cyber attack Pierluigi Paganini November 29, 2024 Zello urges customers with accounts…
The Commonwealth Bank of Australia is continuing down its generative AI path with the emerging technology now embedded into a…
The US Federal Trade Commission has opened a broad antitrust investigation into Microsoft, including of its software licensing and cloud…
GMHBA, a Geelong-based private health insurer and healthcare provider, has appointed Kathryn Young as its new chief information officer. Image…
Nov 28, 2024Ravie LakshmananIoT Security / Vulnerability Nearly two dozen security vulnerabilities have been disclosed in Advantech EKI industrial-grade wireless…
The Tor Project has put out an urgent call to the privacy community asking volunteers to help deploy 200 new…
APT-C-60 launched a phishing attack in August 2024, targeting domestic organizations with malicious emails disguised as job applications. These emails,…
Helldown Ransomware, a sophisticated cyber threat, actively targets critical industries worldwide by leveraging advanced cross-platform capabilities, including Windows and Linux,…
A cyberattack impacted operations at UK Wirral University Teaching Hospital Pierluigi Paganini November 28, 2024 UK’s Wirral University Teaching Hospital…
UNC2465, a financially motivated threat actor, leverages the SMOKEDHAM backdoor to gain initial access to target networks, which are often…
For the past two days, social media platforms have been abuzz with claims that Microsoft, the software giant, has been…