A major illegal piracy streaming service was dismantled in a joint operation led by Italy’s Postal and Cybersecurity Police Service,…
ESET Research has discovered the first UEFI bootkit designed for Linux systems, named Bootkitty by its creators. Researchers believe this…
Browse by Chapter Click on the tiles below to see how digital is transforming the HR department in Australian business. …
A newly discovered malware, dubbed GodLoader, is raising alarms in the cybersecurity community for its ability to stealthily infect devices…
Merseyside residents are facing a third day of significant disruption to healthcare services in the area, following a major cyber…
Browse by Chapter Click on the tiles below to see how digital is transforming the HR department in Australian business. …
VMware fixed five vulnerabilities in Aria Operations product Pierluigi Paganini November 27, 2024 Virtualization giant VMware addressed multiple vulnerabilities in…
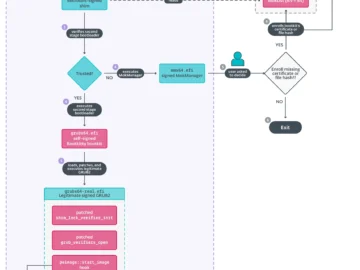
Analysts often face an overwhelming number of threats daily, each demanding a detailed examination to understand its behavior and potential…
In 2019, a ransomware attack hit LifeLabs, a Canadian medical testing company. The ransomware encrypted the lab results of 15…
The government has invited former subpostmasters to a meeting to discuss its response to evidence that a second Post Office…
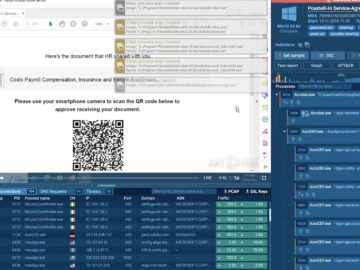
Breaches of major U.S. telecom networks by the China-linked Salt Typhoon group have received widespread media attention, but a second…
An international law enforcement operation has dismantled a pirate streaming service that served over 22 million users worldwide and made €250 million…