Dec 09, 2024The Hacker NewsIdentity Security / Passwordless Identity security is all the rage right now, and rightfully so. Securing…
Dave Moyes, partner, information and digital systems, at SimpsonHaugh Architects, is an industry veteran. He has spent 20 years as…
Google has officially launched Vanir, a groundbreaking open-source security patch validation tool designed to enhance the efficiency and accuracy of…
Raspberry Pi, a pioneer in affordable and programmable computing, has once again elevated its game with the launch of the Raspberry…
Dec 09, 2024Ravie LakshmananArtificial Intelligenc / Vulnerability Details have emerged about a now-patched security flaw in the DeepSeek artificial intelligence…
A cybersecurity researcher has unveiled an unexpected discovery that demonstrates how a simple Cross-Site Scripting (XSS) vulnerability can be leveraged…
A newly disclosed transaction-relay jamming vulnerability has raised concerns about the security of Bitcoin nodes, particularly in the context of…
The High Court in London has ordered that a blogger who was tortured over his political views can take legal…
The Indian Computer Emergency Response Team (CERT-In), the national nodal agency for responding to cybersecurity threats, has issued a vulnerability…
The rise of Application Programming Interfaces (APIs) has revolutionized how businesses operate, enabling seamless connectivity, data sharing, and enhanced functionalities…
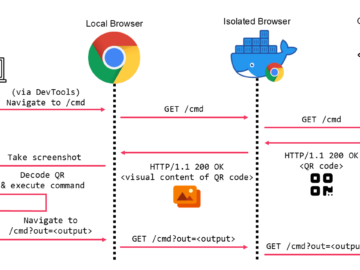
Mandiant devised a technique to bypass browser isolation using QR codes Pierluigi Paganini December 09, 2024 Mandiant revealed a technique…
A critical security vulnerability has been discovered in Qlik Sense Enterprise for Windows, potentially allowing attackers to execute remote code…