Hackers are actively exploiting a critical authentication vulnerability in ProjectSend, a popular open-source file-sharing web application. The vulnerability, now identified…
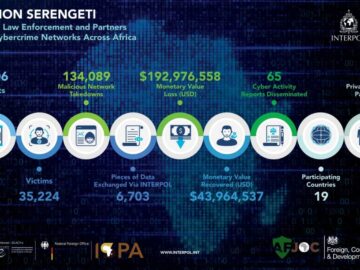
Group-IB collaborated with INTERPOL and AFRIPO in a major crackdown on cybercrime in Africa for “Operation Serengeti.” This article provides…
Cybersecurity experts at ANY.RUN have uncovered an active zero-day attack campaign that leverages corrupted files to bypass antivirus software, sandbox…
Cebu, Philippines, November 27th, 2024, CyberNewsWire Cebu-based entrepreneur Brian Christopher Aguilar has emerged as a notable figure in the cryptocurrency…
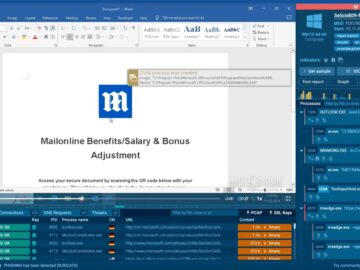
Nov 27, 2024Ravie LakshmananMalware / Cyber Espionage The threat actor known as APT-C-60 has been linked to a cyber attack…
A Manchester law firm has started on-boarding clients for a probable class action against Microsoft and Google, which it believes…
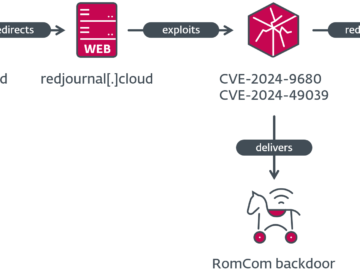
A Russia-aligned hacking group, known as RomCom (also identified as Storm-0978, Tropical Scorpius, or UNC2596), has successfully exploited two zero-day…
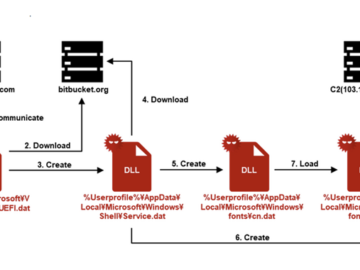
Researchers have uncovered the first UEFI bootkit designed specifically for Linux systems, named Bootkitty. This discovery marks a pivotal moment…
Two Dutch political parties, GroenLinks-PvdA and NSC, have presented a detailed proposal advocating for a Dutch cloud infrastructure to prevent…
How DSPM Helps Businesses Meet Compliance Requirements Pierluigi Paganini November 27, 2024 Data Security Posture Management (DSPM) helps monitor, secure,…
Mozilla has officially launched Firefox 133.0, introducing a host of new features, performance improvements, and critical security fixes. The release,…
Russian group RomCom exploited Firefox and Tor Browser zero-days to target attacks Europe and North America Pierluigi Paganini November 27,…