Experts believe the operation is based in China and relies on a drop-shipping scheme. “It’s likely just a reshipper selling…
SUMMARY Malicious NPM Package Identified: “ethereumvulncontracthandler” disguises as a vulnerability scanner but installs Quasar RAT malware. Technical Details: The package…
Jan 03, 2025Ravie LakshmananMachine Learning / Vulnerability Cybersecurity researchers have shed light on a new jailbreak technique that could be…
Only two of the top 100 listed companies in the Middle East reported cyber security incidents last year, according to…
Federal authorities have unsealed an indictment against a U.S. Army soldier, accusing him of selling and attempting to sell stolen…
72 Hours to Audit-Ready API Security APIs present a unique challenge in this landscape, as risk assessment and mitigation are…
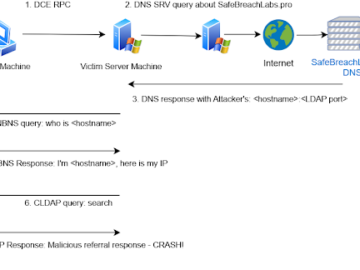
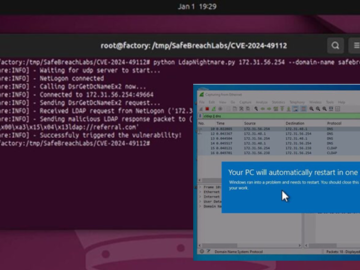
LDAPNightmare, a PoC exploit targets Windows LDAP flaw CVE-2024-49113 Pierluigi Paganini January 03, 2025 Experts warn of a new PoC…
A malicious npm campaign that poses as the Hardhat plugins and the Nomic Foundation is observed to target Ethereum developers…
Around 3.3 million POP3 and IMAP mail servers lack TLS encryption Pierluigi Paganini January 03, 2025 Over 3 million POP3…
Do Hyeong Kwon, the co-founder and former CEO of Terraform Labs, was extradited from Montenegro and appeared in federal court…
Jan 03, 2025Ravie LakshmananWindows Server / Threat Mitigation A proof-of-concept (PoC) exploit has been released for a now-patched security flaw…
NTT Docomo, one of Japan’s leading telecommunications and IT service providers, experienced a massive disruption on January 2, 2025, after…