A large number of Americans’ metadata has been stolen in the sweeping cyberespionage campaign carried out by a Chinese hacking…
Burnout in SOCs: How AI Can Help Analysts Focus on High-Value Tasks Pierluigi Paganini December 05, 2024 SOC analysts, vital…
Latrodectus is a versatile malware family that employs advanced tactics to infiltrate systems, steal sensitive data, and evade detection. Named…
A large U.S. organization with significant operations in China fell victim to a sophisticated cyber attack, likely orchestrated by China-based…
Researchers released a detailed report on a significant security vulnerability named CVE-2023-49785, affecting the ChatGPT Next Web, popularly known as…
In an era where innovation often outpaces implementation, legacy systems remain a hidden yet significant threat to cybersecurity. A recent…
Europol has supported the dismantling of a sophisticated criminal network responsible for facilitating large-scale online fraud. In an operation led…
A years-long infiltration into the systems of eight telecom giants, including AT&T and Verizon, allowed a state sponsored actor to…
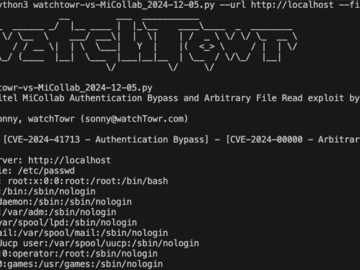
Dec 05, 2024Ravie LakshmananVulnerability / IoT Security Cybersecurity researchers have released a proof-of-concept (PoC) exploit that strings together a now-patched…
Over the past year, artificial intelligence (AI) has proved its worth as a long-term investment for businesses. It brings a…
Citigroup began rolling out new artificial intelligence tools to be used by employees in eight countries, senior executives said. Around…
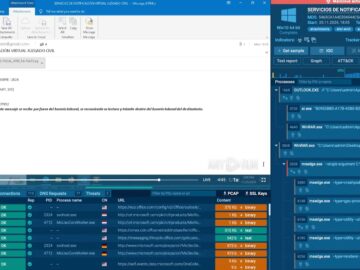
Analyzing phishing attacks have become challenging as these threats continue to evolve in complexity, employing more sophisticated techniques to bypass…