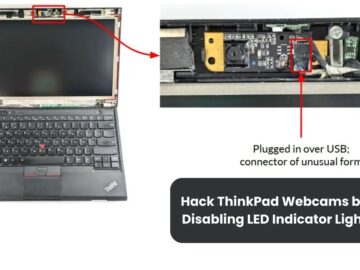
In a presentation at the POC 2024 conference, cybersecurity expert Andrey Konovalov revealed a novel method for covertly disabling the…
A significant development for the tech community is the identification of 2 critical vulnerabilities in several versions of a widely-used…
In a recent study, cybersecurity researchers have unveiled a new side-channel attack that threatens the privacy of users interacting with…
Today’s world is powered by technology. Most day-to-day business operations are underpinned by online systems and digitally stored data. And,…
Nov 30, 2024Mohit KumarRansomware / Cybercrime A Russian cybercriminal wanted in the U.S. in connection with LockBit and Hive ransomware…
Notorious ransomware programmer Mikhail Pavlovich Matveev arrested in Russia Pierluigi Paganini November 30, 2024 Russian authorities arrested ransomware affiliate Mikhail…
2025 promises to be a pivotal year for corporate leaders. Technological advancements, geopolitical shifts, and heightened risks demand unprecedented vigilance…
Anyone who has ever used a printer likely has had a frustrating experience at some point. There always seems to…
A new phishing-as-a-service (PhaaS) platform named ‘Rockstar 2FA’ has emerged, facilitating large-scale adversary-in-the-middle (AiTM) attacks to steal Microsoft 365 credentials….
Free unofficial security patches have been released through the 0patch platform to address a zero-day vulnerability introduced over two years…
Russian law enforcement has arrested and indicted notorious ransomware affiliate Mikhail Pavlovich Matveev (also known as Wazawaka, Uhodiransomwar, m1x, and…
Mastercard is on track to phase out passwords by 2028 and will also eliminate the use of card numbers and…