A sophisticated Windows Remote Access Trojan (RAT) called ElizaRAT has been developed by the APT36 (also known as Transparent Tribe)…
A publicly exposed database has left the sensitive information of hundreds of thousands of individuals vulnerable to potential misuse. Not…
Riyadh, Saudi Arabia, November 29, 2024 – Cyble, among the world’s fastest-growing AI-powered cybersecurity companies, is proud to announce a…
Endpoint detection and response (EDR) tools offer businesses that employ hybrid work models or remote employees an extra layer of…
Nov 29, 2024Ravie LakshmananAI Security / Cloud Security Microsoft has addressed four security flaws impacting its artificial intelligence (AI), cloud,…
A critical vulnerability affecting laptop webcams, specifically on ThinkPad X230 models has been recently discovered as demonstrated by the Andrey…
This newfound push appears to have yielded several fresh experiments with exoskeleton technology in recent years. In 2018, Lockheed Martin…
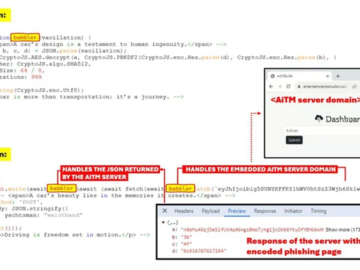
Nov 29, 2024Ravie LakshmananCybercrime / Cloud Security Cybersecurity researchers are warning about malicious email campaigns leveraging a phishing-as-a-service (PhaaS) toolkit…
While most organizations today remain aware of the ongoing cybersecurity threats, there is a constant struggle to keep pace with…
Cyber risk management accounts for the probability of attacks on operational technology (OT) at large industrial facilities, including all the…
Zyxel Firewalls have become a key target in recent cyberattacks, with attackers exploiting a critical vulnerability to deploy the dangerous…
A sophisticated phishing scam targeting corporate internet banking users has emerged in Japan, prompting authorities to issue urgent warnings to…