The xattr command in Unix-like systems allows for the embedding of hidden metadata within files, similar to Windows ADS, known…
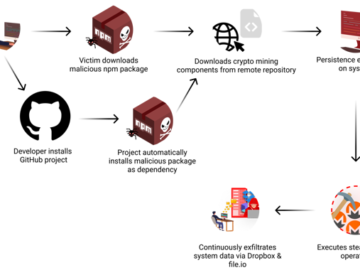
Nov 28, 2024Ravie LakshmananSoftware Security / Data Breach Cybersecurity researchers have discovered a software supply chain attack that has remained…
In today’s dynamic threat landscape, security leaders are under constant pressure to make informed choices about which solutions and strategies…
The Australian government has passed the new Cyber Security Act, which was recently approved by Parliament. One of the most…
Major UK healthcare provider Wirral University Teaching Hospital (WUTH), part of the NHS Foundation Trust, has suffered a cyberattack that caused…
A series of vulnerabilities have been identified, posing significant risks to the system’s security. These vulnerabilities could allow attackers to…
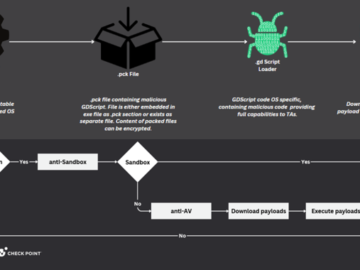
Nov 28, 2024Ravie LakshmananWindows Security / Cryptomining A popular open-source game engine called Godot Engine is being misused as part…
A new and dangerous malware campaign known as PixPirate has been targeting users in recent months, primarily in Brazil and…
A new vulnerability has been discovered in Windows 11, specifically affecting the 23H2 version. This vulnerability is identified in the ksthunk.sys driver,…
Oracle’s Agile Product Lifecycle Management (PLM) software has been flagged for a security vulnerability (CVE-2024-21287) by CERT-In (Computer Emergency Response Team…
Protect Websites & APIs from Malware Attack Malware targeting customer-facing websites and API applications poses significant risks, including compliance violations,…
Microsoft has recently released patches addressing multiple vulnerabilities that could enable attackers to elevate privileges across various Microsoft products. The…