A recent ransomware attack targeting Blue Yonder, a company providing supply chain software, has caused notable disruptions in the IT…
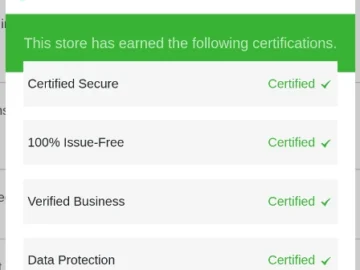
Building fake, fraudulent online stores has never been easier: fraudsters are registering domain names for a pittance, using the SHOPYY…
Nov 26, 2024Ravie LakshmananVulnerability / Cybercrime The Russia-aligned threat actor known as RomCom has been linked to the zero-day exploitation…
Encouraging the public sector to ramp up its adoption of automation and generative artificial intelligence (AI) tools could generate annualised…
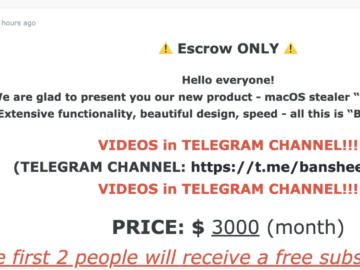
The source code of Banshee Stealer leaked online Pierluigi Paganini November 26, 2024 Banshee Stealer, a MacOS Malware-as-a-Service, shut down…
A 31-year-old Kansas City man has been indicted on federal charges for allegedly hacking into the computer systems of a…
Several high-severity vulnerabilities have been identified in Android and Google Pixel devices, exposing millions of users to potential security risks….
Stalkerware, a type of malicious software that allows someone to secretly monitor and track another person’s device, has become a…
Russia-aligned APT group RomCom was behind attacks that leveraged CVE-2024-9680, a remote code execution flaw in Firefox, and CVE-2024-49039, an…
Thank you for joining! Access your Pro+ Content below. 26 November 2024 The Most Influential Women in UK Technology 2024…
U.S. CISA adds Array Networks AG and vxAG ArrayOS flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini November 26, 2024…
SpyLoan apps, a type of PUP, are rapidly increasing, exploiting social engineering to deceive users into granting excessive permissions, where…