Microsoft and the Justice Department have seized over 240 domains used by customers of ONNX, a phishing-as-a-service (PhaaS) platform, to…
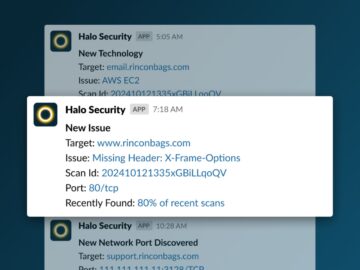
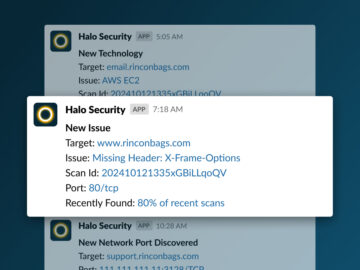
Halo Security, a leader in external attack surface management and penetration testing, has announced the launch of its new Slack®…
Halo Security, a leader in external attack surface management and penetration testing, has announced the launch of its new Slack®…
Five alleged members of the notorious Scattered Spider hacking group have been charged with executing a sophisticated phishing scheme that…
MIAMI, Florida, November 21st, 2024, CyberNewsWire Halo Security, a leader in external attack surface management and penetration testing, has announced…
Nov 21, 2024Ravie LakshmananVulnerability / Cyber Attack As many as 2,000 Palo Alto Networks devices are estimated to have been…
The United States’ Department of Justice (DoJ) yesterday unsealed criminal charges against five individuals, including a 22 year-old British national…
A critical vulnerability in AnyDesk, a popular remote desktop application, has been discovered that could allow attackers to expose users’…
MIAMI, Florida, November 21st, 2024, CyberNewsWire Halo Security, a leader in external attack surface management and penetration testing, has announced…
Law enforcement unsealed criminal charges against five alleged members of Scattered Spider, who allegedly targeted employees of companies nationwide with…
The U.S. has seized the cybercrime website ‘PopeyeTools’ and unsealed charges against three of its administrators, Abdul Ghaffar, Abdul Sami,…
Persistence mechanisms play a critical role in modern cyberattacks, helping malware remain active on compromised systems even after reboots, log-offs,…