A data breach at an unnamed French hospital exposed the medical records of 750,000 patients after a threat actor gained…
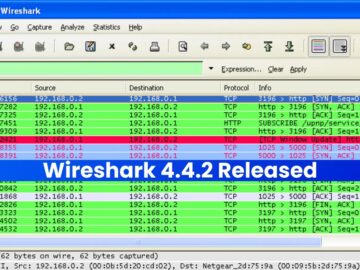
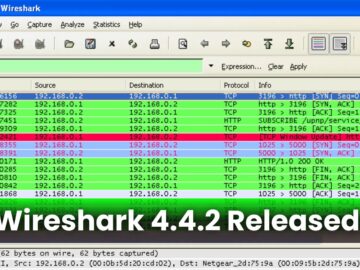
The Wireshark Foundation has announced the release of Wireshark 4.4.2, the latest version of its widely-used network protocol analyzer. This…
The Wireshark Foundation has officially announced the release of Wireshark 4.4.2, the latest version of the world’s most popular network…
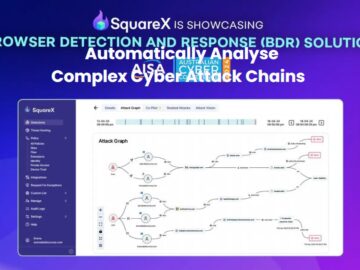
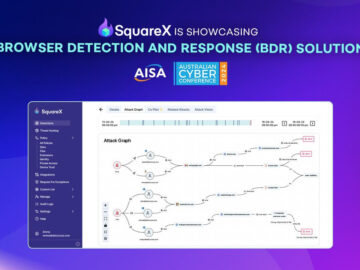
SquareX, the leading browser security company, will make its Australian debut at Melbourne CyberCon 2024, hosted by AISA (Australian Information…
SquareX, the leading browser security company, will make its Australian debut at Melbourne CyberCon 2024, hosted by AISA (Australian Information…
Apple addressed two actively exploited zero-day vulnerabilities Pierluigi Paganini November 20, 2024 Apple released security updates for iOS, iPadOS, macOS,…
MITRE has shared this year’s top 25 list of the most common and dangerous software weaknesses behind more than 31,000…
Palo Alto, California, November 20th, 2024, CyberNewsWire SquareX, the leading browser security company, will make its Australian debut at Melbourne…
There’s no denying that for knowledge workers, most daily activities have moved to virtual platforms. From lead generation and job…
Ford data breach involved a third-party supplier Pierluigi Paganini November 20, 2024 Ford investigates a data breach linked to a…
Finastra has confirmed it warned customers of a cybersecurity incident after a threat actor began selling allegedly stolen data on…
Australia said it was concerned that one in 10 cyber security incidents last year involved critical infrastructure, with state-sponsored actors…