Protect traveler data with these tips: use VPNs, manage app permissions, and secure travel documents. Travel companies should encrypt data,…
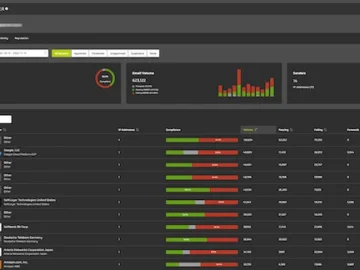
Hornetsecurity launched DMARC Manager, an advanced tool addresses the complex challenges organisations face in managing DMARC, DKIM, and SPF configurations,…
Artificial intelligence tools like ChatGPT, Claude, Google Gemini, and Meta AI represent a stronger threat to data privacy than the…
Microsoft announced today at its Ignite annual conference in Chicago, Illinois, that it’s expanding its bug bounty programs with Zero…
A critical vulnerability in the Windows Kerberos authentication protocol poses a significant risk to millions of servers. Microsoft addressed this…
The AMD-powered El Capitan supercomputer, housed at the Lawrence Livermore National Laboratory (LLNL), is now ranked as the world’s fastest…
These days remote workers in home offices using residential WiFi must maintain a similar security posture as a full-on corporation…
Nov 19, 2024The Hacker NewsInsider Threat / Credential Security Privileged accounts are well-known gateways for potential security threats. However, many…
The Justice Department unsealed criminal charges against Evgenii Ptitsyn, 42, a Russian national, for allegedly administering the sale, distribution, and…
Frustration with slow financial redress could trigger the nuclear option for former subpostmasters who have campaigned for justice since 2009….
Satellite and space technology leader Maxar Space Systems has suffered a data breach. “Our information security team discovered that a…
Spotify playlists and podcasts are being abused to push pirated software, game cheat codes, spam links, and “warez” sites. By…