Ford Motor Company, the American multinational automobile manufacturer, is reportedly investigating a potential data breach after hackers claimed to have…
Oracle has released a security patch for CVE-2024-21287, a remotely exploitable vulnerability in the Oracle Agile PLM Framework that is,…
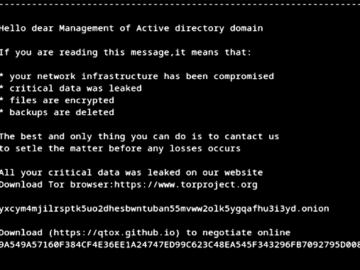
Cybersecurity researchers have shed light on a Linux variant of a relatively new ransomware strain called Helldown, suggesting that the…
Thank you for joining! Access your Pro+ Content below. 19 November 2024 Adventures in AI at Tripadvisor Share this item…
A 42-year-old Russian national, Evgenii Ptitsyn has been extradited from South Korea to the United States to face charges related…
On the campaign trail and in recent days, Donald Trump has detailed extensive plans for immigration crackdowns and mass deportations…
AlmaLinux is a free, open-source, enterprise-grade Linux distribution. Governed and owned by the community, it offers a production-ready platform with…
Cloud-based human capital and technology-enabled services provider Alight has announced a partnership with Microsoft expert Avanade to integrate its Worklife…
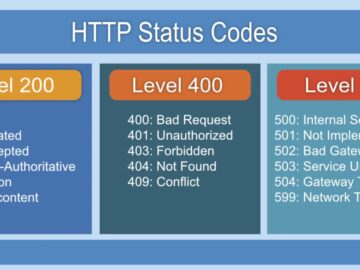
In the Internet world, there are five different categories for HTTP status codes, which are used to indicate the result…
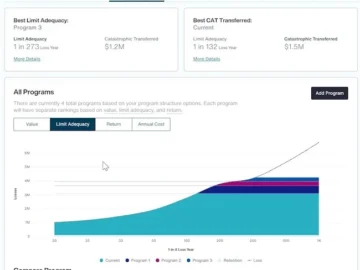
Aon launched its Cyber Risk Analyzer, a digital application that allows risk managers to make data-driven, technology-enabled decisions to mitigate…
Nationwide Building Society is drawing on HPE’s private cloud capabilities to help deliver on the next phase of its multi-year…
U.S. CISA adds Progress Kemp LoadMaster, Palo Alto Networks PAN-OS and Expedition bugs to its Known Exploited Vulnerabilities catalog Pierluigi…