Brave Browser 1.71 for iOS introduces a new privacy-focused feature called “Shred,” which allows users to easily delete site-specific mobile…
T-Mobile has confirmed that it was hit during a recent wave of telecom network breaches attributed to a China-linked threat…
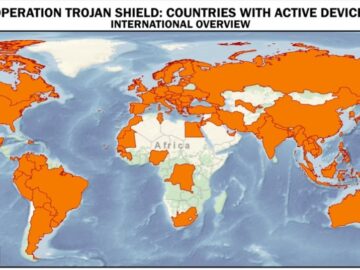
A critical player in one of the world’s largest law enforcement sting operations has been sentenced to 63 months in…
Palo Alto Networks has finally released security updates for two actively exploited zero-day vulnerabilities in its Next-Generation Firewalls (NGFW). The first…
The United States secured the extradition of a Russian national from South Korea who is allegedly the mastermind behind the…
Coles Group is strengthening its digital offerings with new in-app features, technology trials and omnichannel engagement. Coles Group’s chief digital…
Hackers breached U.S. satellite maker Maxar Space Systems and accessed personal data belonging to its employees, the company informs in…
A German court said that Facebook users whose data was illegally obtained in 2018 and 2019 were eligible for compensation….
Recently disclosed VMware vCenter Server bugs are actively exploited in attacks Pierluigi Paganini November 18, 2024 Threat actors are actively…
A Facebook malvertising campaign disguised as Bitwarden updates spreads malware, targeting business accounts. Users are tricked into installing malicious Chrome…
Australia’s competition regulator is seeking views on the Macquarie-backed telecommunications group Vocus’ $5.25 billion takeover of local telecom operator TPG…
Evgenii Ptitsyn, a Russian national and suspected administrator of the Phobos ransomware operation, was extradited from South Korea and is…