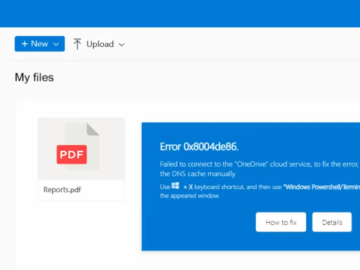
A threat actor known as BrazenBamboo has exploited an unresolved security flaw in Fortinet’s FortiClient for Windows to extract VPN…
The NSO Group, an Israeli surveillance technology firm, is facing significant legal challenges after a U.S. court filing revealed damning…
OpenBSD has released an important bug fix addressing a potential double-free vulnerability within its Network File System (NFS) client and…
Glove Stealer bypasses Chrome’s App-Bound Encryption to steal cookies Pierluigi Paganini November 16, 2024 The Glove Stealer malware exploits a…
Integrating AI into SOCs The integration of AI into security operations centers (SOCs) and its impact on the workforce are…
What is HAQL? Back in 2022, we were faced with a challenge: we wanted to build useful, actionable dashboards for…
Israeli surveillance firm NSO Group reportedly used multiple zero-day exploits, including an unknown one named “Erised,” that leveraged WhatsApp vulnerabilities…
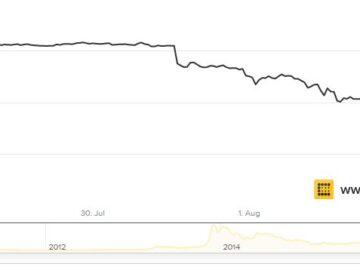
A popular European football club and a media giant are the latest in a growing list of organizations to abandon…
Bitfinex hacker Ilya Lichtenstein was sentenced to 5 years in prison Pierluigi Paganini November 15, 2024 Bitfinex hacker, Ilya Lichtenstein,…
A malware botnet is exploiting a zero-day vulnerability in end-of-life GeoVision devices to compromise and recruit them for likely DDoS…
On Friday, the U.S. Federal Trade Commission (FTC) reported that the number of consumer complaints about unwanted telemarketing phone calls…
by Gary S. Miliefsky, CISSP, fmDHS As the publisher of Cyber Defense Magazine, I have a great honor and pleasure…