GitHub has released a critical security advisory highlighting vulnerabilities that merit immediate action from users of GitHub Enterprise Server (GHES)….
Dutch, French, and German police forces arrested three members of a notorious criminal network responsible for a series of violent…
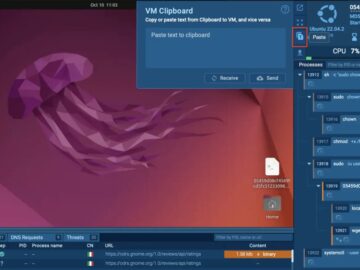
ANY.RUN upgraded its Linux sandbox with features to enhance malware analysis. It now uses a stable Chrome browser for smoother interaction with…
The modern Security Operations Center (SOC) has morphed and matured since its infancy in the early 1990s. The primary responsibility…
Deleting your personal data from 23andMe is proving to be hard. There are good reasons for people wanting to delete…
Sir Alan Bates has told prime minister Keir Starmer that if government is not capable of completing financial redress for…
A critical vulnerability has been discovered in multihomed Linux devices. It allows attackers to spoof and inject packets into internal…
The researchers say that if the attack were carried out in the real world, people could be socially engineered into…
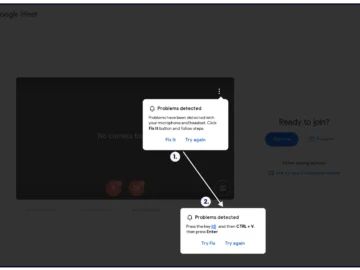
Users of the Google Meet video communication service have been targeted by cyber crooks using the ClickFix tactic to infect…
The UK’s cyber security chief has warned of a widening gap between the escalating cyber threats faced by the UK…
Cybersecurity analysts at Microsoft recently discovered that their customers face more than 600 million cyber-attacks every day. The current cyber…
From the ground, northeastern Norway might look like fjord country, peppered with neat red houses and dissected by snowmobile tours…