AI-based chatbots are increasingly becoming integral to our daily lives, with services like Gemini on Android, Copilot in Microsoft Edge,…
Norway has increased the scope of an already-ambitious multi-branched technology expansion plan by establishing a National Digitisation Forum (NDF), tasked…
The majority of business leaders polled in a recent survey for Kyndryl (94%) list technology modernisation as a high priority…
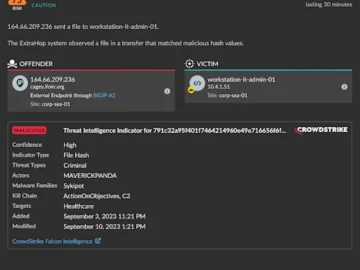
ExtraHop unveiled new network-based file analysis capabilities in ExtraHop RevealX to detect malware, combat ransomware, and help prevent data loss….
Oct 16, 2024Ravie LakshmananData Privacy / Passwordless The FIDO Alliance said it’s working to make passkeys and other credentials more…
The North Korean hacking group ScarCruft launched a large-scale attack in May that leveraged an Internet Explorer zero-day flaw to…
Millions of people are turning normal pictures into nude images, and it can be done in minutes. Journalists at Wired…
Google Cloud continues to gain traction as businesses roll out artificial intelligence (AI). Its data management and analytics tools are…
Commonwealth Bank has incurred a second spam-related fine in as many years, this time for sending over 170 million messages…
Amazon has seen massive adoption of passkeys since the company quietly rolled them out a year ago, announcing today that…
A joint report by AhnLab Security Emergency response Center (ASEC) and the National Cyber Security Center (NCSC) has revealed a…
In today’s rapidly evolving digital landscape, organizations are increasingly reliant on complex networks of identities to power their operations. From…