The CRA will be a game-changing regulation for software and connected product security. The CRA imposes cybersecurity requirements for manufacturers…
If you’re managing an SIEM (Security Information and Event Management) system, you know how vital centralized threat detection is. SIEM…
Finnish Customs and Swedish Police, with Bitdefender’s support, shut down dark web marketplaces Sipulitie and Tsätti. These platforms facilitated the…
Oct 15, 2024Ravie LakshmananMobile Security / Financial Fraud New variants of an Android banking trojan called TrickMo have been found…
Google has signed what it claims is the world’s first corporate agreement to purchase nuclear energy from multiple small modular…
EDRSilencer is a tool designed to enhance data privacy and security by “silencing” or “blocking” unwanted data transmissions from endpoints….
The Cerberus Android banking trojan, which gained notoriety in 2019 for its ability to target financial and social media apps,…
Oct 15, 2024Ravie LakshmananFinancial Fraud / Linux North Korean threat actors have been observed using a Linux variant of a…
Improving productivity in policing through technology and digital skills can create the equivalent of 30,000 more police officers and staff,…
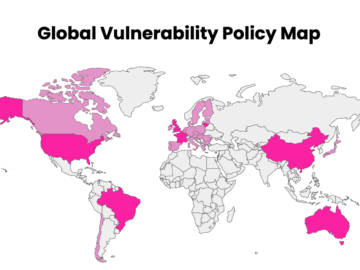
To help organizations keep up with the shifting landscape of VDP mandates and recommendations, HackerOne has developed the Global Vulnerability…
A code signing certificate is a digital certificate that allows software developers to sign their applications. This ensures both the…
The Horus Protector crypter is being used to distribute various malware families, including AgentTesla, Remcos, Snake, NjRat, and others, whose…