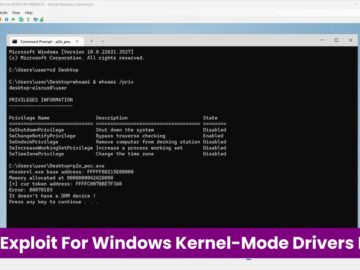
A critical vulnerability in Windows Kernel-Mode Drivers has been exposed with the release of a Proof-of-Concept (PoC) exploit, allowing attackers…
Kate Ruane, director of the Center for Democracy and Technology’s free expression project, says most major technology platforms now have…
A critical vulnerability in Fortinet’s FortiGate SSLVPN appliances, CVE-2024-23113, has been actively exploited in the wild. This format string flaw…
GitLab has announced the release of critical patches for its Community Edition (CE) and Enterprise Edition (EE) with versions 17.4.2,…
WordPress Jetpack plugin critical flaw impacts 27 million sites Pierluigi Paganini October 15, 2024 WordPress Jetpack plugin issued an update…
A group of threat actors, led by the notorious hacker known as IntelBroker, has claimed responsibility for a significant data…
A recently identified vulnerability in Ubuntu’s Authd, CVE-2024-9312, has raised significant security concerns. The flaw, present through version 0.3.6, allows…
China’s National Computer Virus Emergency Response Center (CVERC) has doubled down on claims that the threat actor known as the…
Google Cloud Platform (GCP) has gone live with its Parallelstore managed parallel file storage service, which is aimed at intensive…
Researchers have uncovered a sophisticated attack campaign targeting Ivanti Cloud Services Appliance (CSA) users. Nation-state actors are exploiting multiple zero-day…
In recent years, third-party breaches have gained significant attention, with high-profile incidents such as the Okta and MOVEit hacks highlighting…
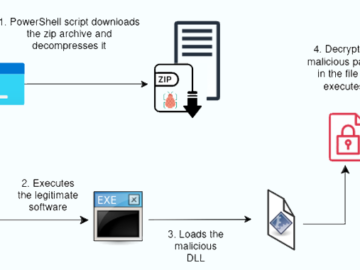
Oct 15, 2024Ravie LakshmananThreat Detection / Malware Cybersecurity researchers have disclosed a new malware campaign that delivers Hijack Loader artifacts…