Cloud hosting provider Rackspace suffered a data breach exposing “limited” customer monitoring data after threat actors exploited a zero-day vulnerability…
A former detective brought in to investigate the confidential sources of two journalists who exposed collusion between police in Northern…
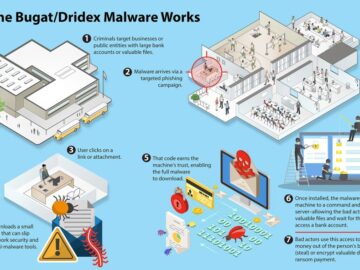
Cyber and law enforcement agencies from the U.K., U.S., and Australia have come together to expose the Russian cybercriminal empire…
UMC Health System diverted patients following a ransomware attack Pierluigi Paganini October 01, 2024 US healthcare provider UMC Health System…
NIS2 focuses on strengthening EU resilience through new and amended obligations for cybersecurity risk management practices, incident reporting, and security…
Today, Microsoft announced the release of Windows 11, version 24H2, the next feature update for its operating system (also known…
An ongoing fake Google Chrome update effort targeting France has been noticed, which spreads WarmCookie malware via compromised websites. WarmCookie…
Paragon was founded in 2019 by veterans from the Israel Defense Forces’ powerful intelligence Unit 8200 with the active involvement…
Texas healthcare provider UMC Health System was forced to divert some patients to other locations after a ransomware attack impacted…
The 8220 hacker group is known for targeting both Windows and Linux web servers by deploying “crypto-jacking” malware to exploit…
International law enforcement has worked for years to disrupt the cybercriminal gang Evil Corp and its egregious global crime spree….
Did you know that over 80% of web applications fail due to poor planning and execution? Now imagine a framework…