Fortinet and Mandiant investigated the mass exploitation of FortiManager devices via CVE-2024-47575, impacting 50+ systems across industries. Threat actor UNC5820…
Malware refers to any form of malicious software which aims to disrupt, harm or steal private information for criminal use….
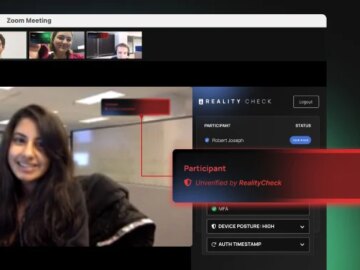
Oct 25, 2024The Hacker NewsArtificial Intelligence / Identity Security Artificial Intelligence (AI) has rapidly evolved from a futuristic concept to…
While Dutch business leaders are highly confident in their IT infrastructure, recent incidents and statistics paint a more concerning picture…
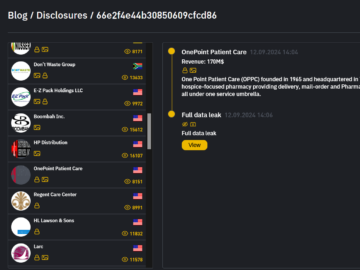
OnePoint Patient Care data breach impacted 795916 individuals Pierluigi Paganini October 25, 2024 US hospice pharmacy OnePoint Patient Care suffered…
UnitedHealth Group (UHG) has confirmed a massive data breach affecting over 100 million American users. This cyberattack, which is being…
Oct 25, 2024Ravie LakshmananRegulatory Compliance / Data Breach The U.S. Securities and Exchange Commission (SEC) has charged four current and…
The surge of artificial intelligence (AI) applications has contributed to unprecedented demand on datacentre infrastructure. Existing facilities are no longer…
From Risk Assessment to Action: Improving Your DLP Response Pierluigi Paganini October 25, 2024 DLP is key in cybersecurity; a…
Security researchers from Aquasec recently discovered a critical vulnerability in the AWS Cloud Development Kit (CDK) that could allow attackers…
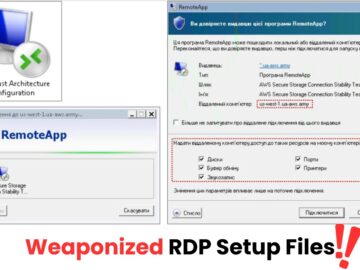
A new sophisticated phishing campaign targeting government agencies, industrial enterprises, and military units in Ukraine and potentially other countries has…
Cyble Research & Intelligence Labs (CRIL) has shared its weekly ICS vulnerability report, highlighting multiple vulnerabilities affecting industrial control systems…