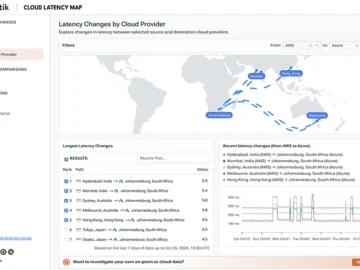
Kentik launched The Cloud Latency Map, a free public tool allowing anyone to explore the latencies measured between over 100…
A magnanimous feat of “Operation Magnus” that took down one of the biggest infostealer operations around the globe is perhaps…
The United States announced charges today against Maxim Rudometov, a Russian national, for being the suspected developer and administrator of…
Hackers target gambling games primarily due to the lucrative financial opportunities they present. The online gambling industry is a rich…
WrnRAT is a new malware attack that cybercriminals have deployed by using popular gambling games like Badugi, Go-Stop, and Hold’em…
Custom generative AI solutions have the potential to transform industries, equipping businesses to reach their goals with exceptional efficiency and…
With 100 years of history, Interpol is the police organization par excellence, bringing together 196 countries in the fight against crime. But…
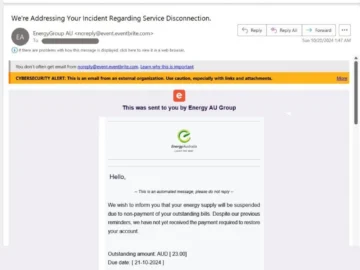
Crooks are leveraging the event management and ticketing website Eventbrite to deliver their phishing emails to potential targets. “Since July,…
Apple has released security patches for most of its operating systems, including iOS, Mac, iPadOS and watchOS. Especially important are…
Oct 29, 2024Ravie LakshmananCybercrime / Malware The Dutch National Police, along with international partners, have announced the disruption of the…
Ireland’s Department of Social Protection has contracted Tata Consultancy Services (TCS) to provide the IT and business services that underpin…
In the modern, globalized business environment, data security and privacy measures are not just necessary but essential, as supply chains…