Security researchers have uncovered multiple vulnerabilities in Realtek’s SD card reader driver, RtsPer.sys, affecting numerous laptops from major manufacturers, including…
Google’s Ambitious Leap: AI to Replace Web Browsers? In a bold move that could redefine how users access information online,…
Jumio unveiled Jumio Liveness, an enhanced, in-house technology designed to address increasingly sophisticated fraud tactics. This solution expands beyond traditional…
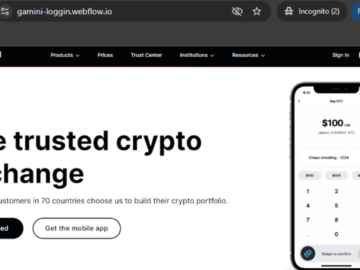
Cybersecurity researchers have warned of a spike in phishing pages created using a website builder tool called Webflow, as threat…
In today’s rapidly evolving digital landscape, the role of the Chief Information Security Officer (CISO) is more critical than ever….
Last week on Malwarebytes Labs: Last week on ThreatDown: Stay safe! Our business solutions remove all remnants of ransomware and…
Black Basta affiliates used Microsoft Teams in recent attacks Pierluigi Paganini October 28, 2024 ReliaQuest researchers observed Black Basta affiliates…
Hong Kong has unveiled its first guidelines for the “responsible” application of artificial intelligence (AI) in the financial sector. Announced…
The recent CrowdStrike outage —a major player in cybersecurity—serves as a critical wake-up call for organizations everywhere. Affecting over 8.5…
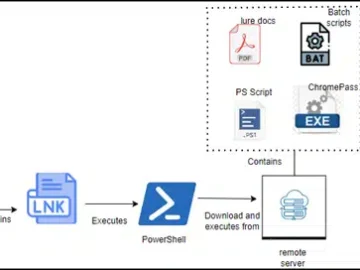
Cyble Research and Intelligence Labs (CRIL) has reported an ongoing cyberattack campaign orchestrated by a persistent threat group known as…
NVIDIA released a critical security update for its GPU Display Driver to fix vulnerabilities that could enable remote code execution,…
Security researchers have discovered and detailed a critical remote code execution (RCE) vulnerability in the VMware vCenter Server, identified as…