AI-based compliance and security management firm Chorology Inc., has introduced a tool aimed at helping businesses manage sensitive data in…
As Halloween approaches, there’s more to be afraid of than the typical ghosts and goblins. In the world of cybersecurity,…
Cisco has added new security features that significantly mitigate brute-force and password spray attacks on Cisco ASA and Firepower Threat Defense…
Chinese cyber spies targeted phones used by Trump and Vance Pierluigi Paganini October 26, 2024 China-linked threat actors targeted the…
Attackers can downgrade Windows kernel components to bypass security features such as Driver Signature Enforcement and deploy rootkits on fully…
SafeBreach Labs unveils ‘Windows Downdate,’ a new attack method which compromises Windows 11 by downgrading system components, and reviving old/ptched…
A serious security vulnerability has been uncovered in Arcadyan routers, stemming from the unexpected presence of Wi-Fi Alliance’s testing software…
The fourth day of Pwn2Own Ireland 2024 marked the end of the hacking competition with more than $1 million in…
Oct 26, 2024Ravie LakshmananCybercrime / Malware Four members of the now-defunct REvil ransomware operation have been sentenced to several years…
Oct 26, 2024Ravie LakshmananCloud Security / Cryptocurrency The infamous cryptojacking group known as TeamTNT appears to be readying for a…
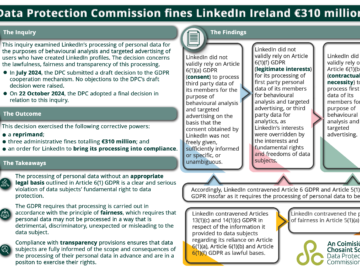
Irish Data Protection Commission fined LinkedIn €310M for GDPR infringement Pierluigi Paganini October 26, 2024 Irish Data Protection Commission fined…
Oct 26, 2024Ravie LakshmananCyber Attack / Threat Intelligence The Computer Emergency Response Team of Ukraine (CERT-UA) has detailed a new…