A critical vulnerability has been discovered in the Common Log File System (CLFS) driver of Windows 11. This flaw enables…
Computer viruses are extremely hazardous, which is why it’s crucial to secure your devices with reliable malware removal programs. These…
Oct 25, 2024Ravie LakshmananCloud Security / Artificial Intelligence Apple has publicly made available its Private Cloud Compute (PCC) Virtual Research…
IR35 status remains an enduring concern for IT contractors when considering their next role, but less so for off-payroll workers…
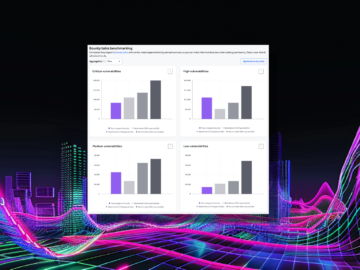
Without clear comparisons and long-term visibility, it’s challenging to identify areas for improvement and make informed, data-driven decisions. That’s why…
Do you know where all the secrets are? The probable answer to this might be NO and believe me you…
This attack had all the hallmarks of ransomware attack and targeted CDK Global systems used by auto dealerships to manage…
Lisle, Ill.-based DeVry University announced the launch of its cutting-edge cyber range platform offering realistic, immersive simulations that mimic real-world cyber threats….
Distributed denial-of-service attacks pose an increasing threat to organizations, with even some of the largest firms suffering significant disruptions from…
False positives in API security are a serious problem, often resulting in wasted results and time, missing real threats, alert…
Fortinet and Mandiant investigated the mass exploitation of FortiManager devices via CVE-2024-47575, impacting 50+ systems across industries. Threat actor UNC5820…
Malware refers to any form of malicious software which aims to disrupt, harm or steal private information for criminal use….