In recent times, WhatsApp users have typically followed a straightforward process when it comes to managing their contacts: they would…
A new Fortinet FortiManager flaw dubbed “FortiJump” and tracked as CVE-2024-47575 has been exploited since June 2024 in zero-day attacks…
DarkComet, a stealthy Remote Access Trojan, silently infiltrates systems, stealing sensitive data like credentials and passwords. It also acts as…
The government claims a data bill introduced in the House of Lords today will improve public services and boost the…
When it comes to privacy and data processing, trust is paramount. And LinkedIn’s €310 million fine by the Irish Data…
On the second day of Pwn2Own Ireland 2024, competing white hat hackers showcased an impressive 51 zero-day vulnerabilities, earning a…
When it comes to protecting your business from increasingly sophisticated cyber threats, a Managed Security Information and Event Management (SIEM)…
24 Oct In a Cloudy World, On-Premises Still Might be The Way To Go Posted at 10:11h in Blogs by…
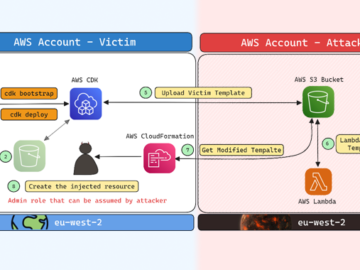
Cybersecurity researchers have disclosed a security flaw impacting Amazon Web Services (AWS) Cloud Development Kit (CDK) that could have resulted…
A critical vulnerability has been identified in the Cisco Adaptive Security Appliance (ASA) Software, posing a significant security risk to…
A cybersecurity researcher discovered a massive data leak exposing over 115,000 sensitive documents associated with the UN Trust Fund to…
Oct 24, 2024Ravie LakshmananVulnerability / Network Security Cisco on Wednesday said it has released updates to address an actively exploited…