The Post Office’s boss met former subpostmasters about the future and was warned the business could not move forward without…
Safe Mode is an operating system diagnostic mode. It is primarily used to troubleshoot issues by loading only essential “drivers”…
The North Korean threat actor known as Lazarus Group has been attributed to the zero-day exploitation of a now-patched security…
In September 2024, the Nairobi Court of Appeal ruled that two cases brought by 185 former Facebook and Instagram content…
GitLab has released new patch versions 17.5.1, 17.4.3, and 17.3.6 for both its Community Edition (CE) and Enterprise Edition (EE)….
As ZachXBT has pursued that career as a crypto vigilante, he has also kept his mask firmly in place. Online,…
Multiple Xerox printer models, including EC80xx, AltaLink, VersaLink, and WorkCentre, have been identified as vulnerable to an authenticated remote code…
In recent years, we have witnessed a significant rise in cybercriminal activities, particularly involving ransomware attacks. These gangs have become…
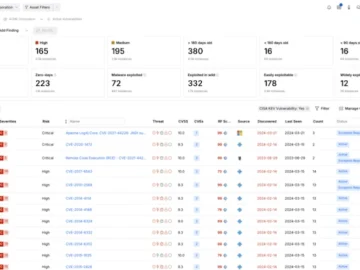
Nucleus Security announced Nucleus POAM Process Automation, a comprehensive solution for federal agencies and their vendors to streamline risk management…
The National Security Agency (NSA) has recently issued a public service announcement emphasizing a simple yet effective action: reboot your…
Cisco has issued a critical security advisory regarding a vulnerability in its Adaptive Security Appliance (ASA) Software. The vulnerability could…
Companies depend on external partners to support operations and provide various services. Collaborating with contractors, consultants and auditors is often…