Data privacy has become a crucial concern for individuals and businesses alike with the cyber world growing to be as…
A crypto draining app mimicking the legitimate ‘WalletConnect’ project has been distributed over Google Play for five months getting more…
NVIDIA has disclosed critical vulnerabilities in its Container Toolkit, potentially allowing attackers to execute remote code. The vulnerabilities, identified as…
Recently, the CEO of the world’s biggest advertising group, Mark Read, was the target of a deepfake scam using an AI-based voice…
The threat actor, formed in 2023, specializes in ransomware attacks targeting Russian government organizations. It encrypts and deletes victim data,…
The importance of internet safety has never been more pronounced than in today’s digital age, where the boundaries between our…
26 Sep Cybersecurity Stocks Could Be A Great Investment Heading Into 2025 Posted at 08:54h in Blogs by Di Freeze…
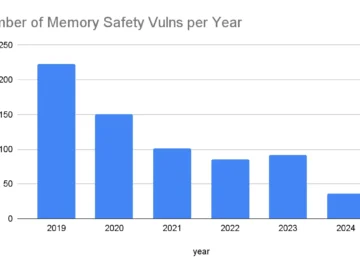
Google’s decision to write new code into Android’s codebase in Rust, a memory-safe programming language, has resulted in a significant…
Sep 26, 2024Ravie LakshmananCyber Attack / Malware Threat actors with ties to North Korea have been observed leveraging two new…
HPE Aruba Networking has fixed three critical vulnerabilities in the Command Line Interface (CLI) service of its Aruba Access Points,…
The Cybersecurity and Infrastructure Security Agency (CISA) released a pivotal new resource to improve the safety and security of K-12…
At the start of September, Nour was having an ordinary evening at home in Beirut—eating pumpkin seeds and watching Netflix—when…