The National Federation of Subpostmasters (NFSP) has written to the minister in charge of the Post Office requesting a review…
SIEM (Security Information and Event Management) is like the nervous system of your security operations. It collects all the threat…
Cyber attackers are using encoded JavaScript files to hide malware, abusing Microsoft’s Script Encoder to disguise harmful scripts in .jse…
It’s estimated that organizations spend more than $200 billion annually on security hardware, software and services globally. That’s a big…
Threat actors have been observed abusing Amazon S3 (Simple Storage Service) Transfer Acceleration feature as part of ransomware attacks designed…
The emergence of large language artificial intelligence (AI) models for programming languages opens up the possibility of AI developers and…
Industry experts and thought leaders will gather to discuss the state of Australia’s Internet of Things (IoT) industry at the…
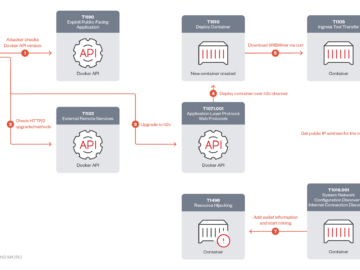
Crooks are targeting Docker API servers to deploy SRBMiner Pierluigi Paganini October 23, 2024 Threat actors are targeting Docker remote…
Millions of iOS and Android users are at risk after Symantec discovered that popular apps contain hardcoded, unencrypted cloud keys….
It may come as a surprise to learn that 34% of security practitioners are in the dark about how many…
Two-thirds of participants in a six-month trial of Microsoft 365 Copilot across the federal government used the tool “a few…
PCI DSS 4.0.1 may have been with us for six months now but the reality is that most entities still…