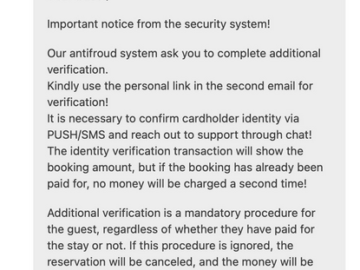
A number of cybercriminal innovations are making it easier for scammers to cash in on your upcoming travel plans. This…
OpenAI’s new “ChatGPT search” Chrome extension feels like nothing more than a typical search hijacker, changing Chrome’s settings so your address…
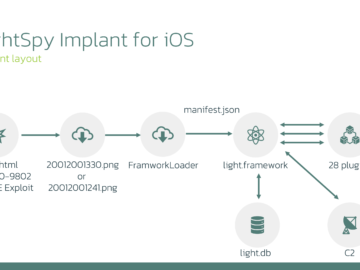
New LightSpy spyware version targets iPhones with destructive capabilities Pierluigi Paganini November 01, 2024 New LightSpy spyware targets iPhones supporting…
Mindgard researchers uncovered critical vulnerabilities in Microsoft’s Azure AI Content Safety service, allowing attackers to bypass its safeguards and unleash…
In a year marked by unprecedented disinformation and cyberattacks, at least we can all come together and laugh at Russia’s…
Synology, a Taiwanese network-attached storage (NAS) appliance maker, patched two critical zero-days exploited during last week’s Pwn2Own hacking competition within…
Let’s not sugarcoat it: phishing is one of the most effective ways cybercriminals worm their way into your network. Why?…
LottieFiles confirmed a supply chain attack on Lottie-Player Pierluigi Paganini November 01, 2024 LottieFiles confirmed a supply chain attack on…
LastPass is warning about an ongoing campaign where scammers are writing reviews for its Chrome extension to promote a fake…
Operation EMERALDWHALE compromises over 15,000 cloud credentials, exploiting exposed Git and Laravel files. Attackers use compromised S3 buckets for storage,…
In what could potentially be the largest data breach in the history of pathology labs in the United States, the…
Researchers at the Satori Threat Intelligence and Research team have published their findings about a group of cybercriminals that infect…