The U.S. Cybersecurity & Infrastructure Security Agency (CISA) is proposing security requirements to prevent adversary states from accessing American’s personal…
Anthropic, a startup backed by Alphabet and Amazon.com, has released a pair of updated artificial intelligence models, along with a…
Microsoft has released the optional KB5045594 preview cumulative update for Windows 10 22H2 with fixes for problems printing to multi-function…
Aurecon has committed to a five-year strategic partnership with Workday that will see it create a roadmap for evolving a…
Multiple popular mobile applications for iOS and Android come with hardcoded, unencrypted credentials for cloud services like Amazon Web Services (AWS)…
The Australian Competition and Consumer Commission (ACCC) is ramping up its cyber security capabilities over the rest of FY25. The…
The SEC has charged four companies—Unisys Corp, Avaya Holdings, Check Point Software, and Mimecast—for allegedly misleading investors about the impact…
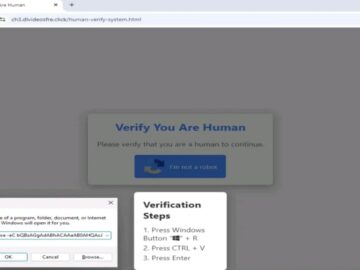
Lumma Stealer malware uses fake CAPTCHA to deceive victims. This information-stealing malware targets sensitive data like passwords and cryptocurrency details….
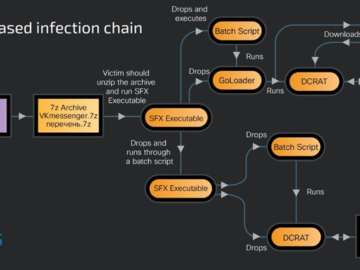
Russian-speaking users have become the target of a new phishing campaign that leverages an open-source phishing toolkit called Gophish to…
Why do organisations invest in Enterprise Resource Planning (ERP) systems? The goal is simple: to make their business more efficient,…
Regulators are betting big on data rights for reshaping financial services, starting with new rules aimed at giving consumers greater…
Proof-of-concept exploit code is now public for a vulnerability in Microsoft’s Remote Registry client that could be used to take control of…