A database containing sensitive, sometimes personal information from the United Nations Trust Fund to End Violence Against Women was openly…
peshkova – stock.adobe.com By Helen Fleming, Executive Director – Search & Specialisms, Harvey Nash Published: 22 Oct 2024 A Chief…
INE Security offers essential advice to protect digital assets and enhance security. As small businesses increasingly depend on digital technologies…
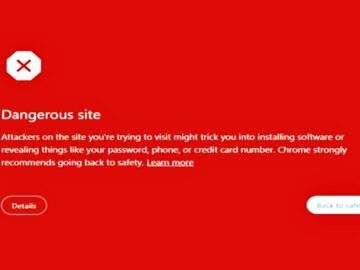
Anti-bot services on the dark web allow phishers to bypass Google’s Red Page warnings, evading detection and making phishing campaigns…
Dutch Central Bank Issues Warning: Keep Cash on Hand In recent weeks, the focus has largely been on the potential…
Samsung zero-day flaw actively exploited in the wild Pierluigi Paganini October 22, 2024 Google’s Threat Analysis Group (TAG) researchers warn…
Cybersecurity researchers have uncovered over 1,000 newly registered malicious domains designed to exploit public interest in the upcoming vote. This…
In the constantly evolving realm of cybersecurity, it is critical for incident responders to be prepared and effective. As cyber…
Cary, NC, October 22nd, 2024, CyberNewsWire INE Security offers essential advice to protect digital assets and enhance security. As small…
Cary, NC, October 22nd, 2024, CyberNewsWire INE Security offers essential advice to protect digital assets and enhance security. As small…
Oct 22, 2024Ravie LakshmananDocker Security / Cloud Security Bad actors have been observed targeting Docker remote API servers to deploy…
Public companies facing cyberattacks must be honest in their disclosures, or the consequences could hit harder than the breach itself….