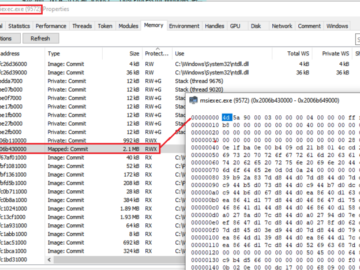
VMware has released another security update for CVE-2024-38812, a critical VMware vCenter Server remote code execution vulnerability that was not…
Akira Ransomware Actors are Developing a Rust Variant to Attack ESXi servers. First identified in March 2023, it targets both…
The Post Office’s head of investigations told public inquiry that, as a result of the Post Office scandal, court rules…
Experts warn of a new wave of Bumblebee malware attacks Pierluigi Paganini October 22, 2024 Experts warn of a new…
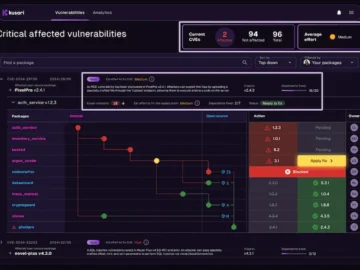
By ingesting Software Bill of Materials (SBOM) data – a list of all software components – the Kusari platform presents…
CNN reports in a special news video that “Fighting cybercrime is big business around the world. By the end of this…
As hybrid cloud-, AI-, and quantum-related risks upend the traditional data security paradigm, IBM is launching IBM Guardium Data Security…
Meta, the company behind Facebook and Instagram says its testing new ways to use facial recognition—both to combat scams and…
Oct 22, 2024Ravie LakshmananVulnerability / Supply Chain Cybersecurity researchers have discovered a number of suspicious packages published to the npm…
The Danish government has relaunched the National Cyber Security Council (NCSC) under the umbrella of a new mission to strengthen…
Splunk has recently issued a security advisory aimed at addressing multiple vulnerabilities within its Splunk Enterprise software. The advisory categorizes…
A critical vulnerability has been identified in the OneDev DevOps platform, posing significant security risks to organizations relying on this…