Researchers have uncovered a massive data breach at MC2 Data, a prominent background check firm. The breach has exposed sensitive…
Microsoft has shared an update on its Secure Future Initiative (SFI), an ambitious program to enhance cybersecurity measures for Microsoft,…
As organizations increasingly migrate to cloud environments, data security remains a paramount concern. The transition to cloud computing offers numerous…
A ransomware attack can inflict severe distress not only on the targeted business and its employees but also on individuals…
In this Help Net Security interview, Jon France, CISO at ISC2, discusses cybersecurity workforce growth. He outlines organizations’ challenges, such…
Recent reports underscore increased fraud losses driven by both old methods and new technologies. As fraudsters exploit advancements in AI…
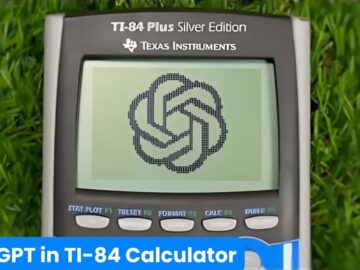
A YouTube creator known as “ChromaLock” has successfully modified a Texas Instruments TI-84 graphing calculator to connect to the internet…
Companies across industries are seeing more bot-driven attacks, both basic and advanced, according to DataDome. An analysis of over 14,000…
Ransomware is seen as the biggest cybersecurity threat across every industry, with 75% of organizations affected by ransomware more than…
In a surprise move, Kaspersky customers in the United States have discovered that their antivirus software has been automatically replaced…
The National Disability Insurance Agency (NDIA) says some people caught up in a data breach last November were under 18…
Virgin Australia is using modules of the SabreMosaic platform to send “ancillary offers” to travellers before they fly, with the…