Often, technology develops faster than we can handle. This is especially true for the federal government and its partners —…
The week was dominated by news that thousands of pagers, walkie-talkies and other devices were exploding across Lebanon on Tuesday…
Ukraine bans Telegram for government agencies, military, and critical infrastructure Pierluigi Paganini September 21, 2024 Ukraine’s NCCC banned the Telegram…
In a major move, the Walt Disney Company announced that it would no longer use Slack for in-house company communication….
The notorious threat actor, IntelBroker, allegedly claimed responsibility for leaking internal communications from Deloitte, a leading global auditing firm. The…
A hacking forum post has raised concerns over a potential Dell Technologies data breach. The breach allegedly affects 10,800 employees…
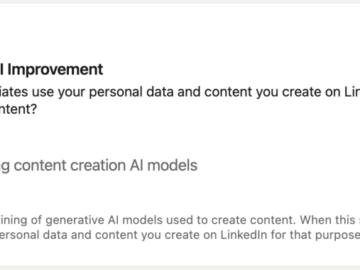
LinkedIn has halted AI model training in the UK after data privacy watchdog and experts raised privacy and ethical concerns….
Tor Project responded to claims that law enforcement can de-anonymize Tor users Pierluigi Paganini September 20, 2024 The maintainers of…
Microsoft has officially announced that Windows Server Update Services (WSUS) is now deprecated, but plans to maintain current functionality and…
Microsoft announced today that Hotpatching is now available in public preview for Windows Server 2025, allowing installation of security updates…
“This is to inform all concerned that the YouTube channel of Supreme Court of India has been taken down. The…
The Walt Disney Company is reportedly ditching Slack after a July data breach exposed over 1TB of confidential messages and files…