US DoJ charged two men with stealing and laundering $230 Million worth of cryptocurrency Pierluigi Paganini September 20, 2024 The…
Madrileña Red de Gas, a regulated natural gas distributor operating in Madrid, was formed in 2010, after being sold off…
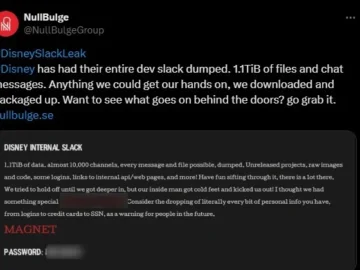
The Walt Disney Company is reportedly severing ties with workplace communications platform Slack. The global entertainment firm apparently took this…
Google has unveiled a new feature in its Password Manager that allows users to sync passkeys across multiple devices. This…
The Vanilla Tempest cybercrime gang used INC ransomware for the first time in attacks on the healthcare sector Pierluigi Paganini…
Mandiant exposed the activities of UNC1860, a sophisticated Iranian state-sponsored cyber group. This group, believed to be affiliated with Iran’s…
GitLab has issued an urgent call to action for organizations using its platform to patch a critical authentication bypass vulnerability….
U.S. CISA adds new Ivanti Cloud Services Appliance Vulnerability to its Known Exploited Vulnerabilities catalog Pierluigi Paganini September 20, 2024…
Operation Kaerb resulted in the arrest of 17 cybercriminals in Argentina, Chile, Colombia, Ecuador, Peru, and Spain. This international operation…
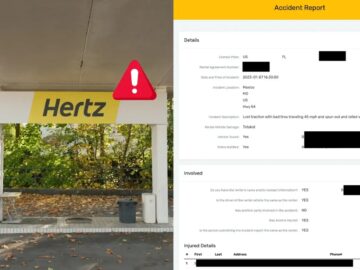
Hertz, a well-known car rental company, has inadvertently exposed over 60,000 insurance claim reports. This breach has raised serious concerns…
Sep 20, 2024Ravie LakshmananEncryption / Digital Security Google on Thursday unveiled a Password Manager PIN to let Chrome web users…
A notorious hacking group known as TeamTNT has resurfaced with a new campaign targeting Virtual Private Server (VPS) infrastructures running…