As the priority for managing digital identities intensifies, organizations are encountering severe identity security risks. Recent findings indicate that many…
Here’s a look at the most interesting products from the past week, featuring releases from anecdotes, F5 Networks, Gcore, Rapid7,…
Nextcloud has launched Nextcloud Hub 9, a significant update to its open-source cloud-based collaboration platform. It introduces several new features…
Internet intelligence firm GreyNoise reports that it has been tracking large waves of “Noise Storms” containing spoofed internet traffic since January 2020. However,…
The U.S. Cybersecurity and Infrastructure Agency (CISA) has added five flaws to its Known Exploited Vulnerabilities (KEV) catalog, among which…
Image: MidjourneyTwo suspects were arrested in Miami this week and charged with conspiracy to steal and launder over $230 million…
Onboarding new employees is an important time for any organization — after all, it’s your opportunity to integrate new team…
German law enforcement seized 47 cryptocurrency exchange services hosted in the country that facilitated illegal money laundering activities for cybercriminals, including…
Despite people generally considering the Tor network as an essential tool for anonymous browsing, german law enforcement agencies have managed…
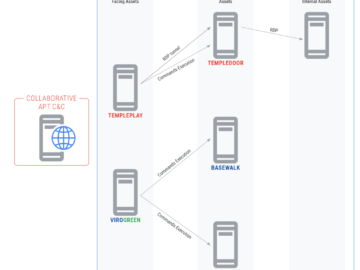
UNC1860, an Iranian state-sponsored threat actor, has emerged as a formidable cyber force in the Middle East. Likely tied to…
Commonwealth Bank is investing in its trading platform CommSec’s digital strategy, putting an emphasis on ease of use and personalisation….
Ivanti warns of a new actively exploited Cloud Services Appliance (CSA) flaw Pierluigi Paganini September 19, 2024 Ivanti warned of…