Researchers discovered a large, Chinese state-sponsored IoT botnet, “Raptor Train,” that compromised over 200,000 SOHO and IoT devices. Operated by…
Nearly three years ago, a new wave of scams emerged, targeting individuals through phone calls and emails. Scammers claimed to…
Sep 19, 2024Ravie LakshmananCyber Attack / Hacking Threat actors have been observed targeting the construction sector by infiltrating the FOUNDATION…
Microsoft has sought to discredit claims that its two biggest public cloud rivals – Amazon and Google – are being…
U.S. CISA adds Microsoft Windows, Apache HugeGraph-Server, Oracle JDeveloper, Oracle WebLogic Server, and Microsoft SQL Server bugs to its Known…
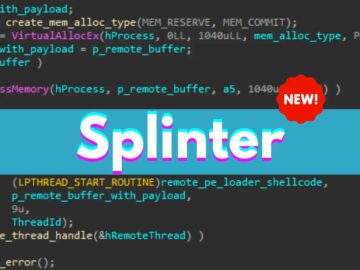
Unit 42 cybersecurity researchers have identified a new post-exploitation red team tool, Splinter, using Advanced WildFire’s memory scanning tools. This…
SambaSpy Attacking Windows Users With Weaponized PDF FilesResearchers discovered a targeted cybercrime campaign in May 2024 that exclusively focused on…
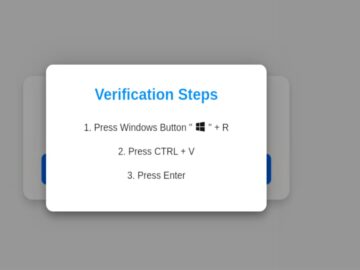
A new phishing campaign uses fake CAPTCHA verification pages to trick Windows users into running malicious PowerShell commands, installing the…
Sep 19, 2024Ravie LakshmananCryptojacking / Cloud Security The cryptojacking operation known as TeamTNT has likely resurfaced as part of a…
A new redress scheme for victims of the Post Office scandal that was launched by the Labour government in July…
A botnet is a network of compromised devices, such as computers and IoT devices, infected with malware and controlled by…
“They don’t trust their smartphones, so they reach back to these more archaic devices, and those blow up. What’s next?”…