In a recent cyberattack, Russian cybersecurity firm Doctor Web (Dr.Web) was forced to disconnect all its servers to mitigate the…
Today, I stumbled upon an interesting quirk while working on a Chrome Extension project using LazyVim. It’s a classic case…
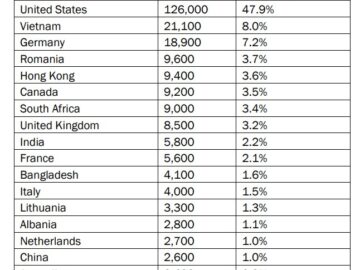
The FBI, in collaboration with U.S. government agencies, dismantled a Chinese state-backed botnet known as Flax Typhoon, comprising 260,000 compromised…
With Gartner recently declaring that SOAR (security orchestration, automation, and response) is being phased out in favor of generative AI-based…
Discord has introduced the DAVE protocol, a custom end-to-end encryption (E2EE) protocol designed to protect audio and video calls on…
A VPN (Virtual Private Network) adds privacy and security to your browsing. But does this make your internet activity truly…
On Tuesday, Russian anti-malware company Doctor Web (Dr.Web) disclosed a security breach after its systems were targeted in a cyberattack…
18 Sep Product Review: Skim Swipe POS Retail Terminal Card Skimmer Detector Posted at 17:01h in Blogs, Videos by Di…
Europol and law enforcement from nine countries successfully dismantled an encrypted communications platform called “Ghost,” which was used by organized crime…
18 Sep Global Penetration Testing Market To Exceed $5 Billion USD Annually By 2031 Posted at 16:30h in Blogs, Videos…
Image: MidjourneyMicrosoft says a ransomware affiliate it tracks as Vanilla Tempest now targets U.S. healthcare organizations in INC ransomware attacks….
U.S. intelligence agencies issued a warning today about a Chinese botnet that has compromised 260,000 devices around the globe, including…