A Cisco Talos researcher worked around the limitations of hardware-level Code Read-out Protection (RDP) on the Socomec DIRIS M-70 gateway by pivoting…
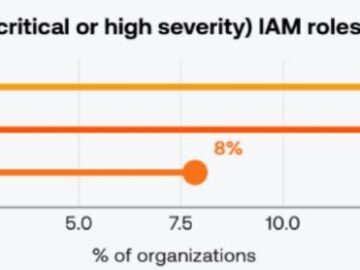
AI adoption is outpacing traditional cyber governance. The “Tenable Cloud and AI Security Risk Report 2026” reveals how overprivileged identities…
Have you ever wondered how many vulnerabilities you’ve missed by a hair’s breadth, due to a single flawed choice? We’ve…
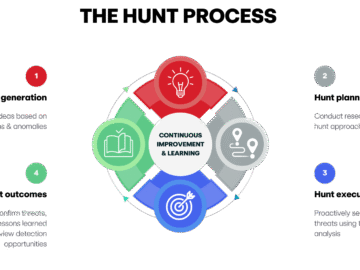
Every CISO knows the uncomfortable truth about their Security Operations Center: the people most responsible for catching threats in real…
I. INTRODUCTION One of the very important issues that red teamers and pentester always have to consider is how to…
The LeakBase cyberforum, considered one of the world’s largest online marketplaces for cybercriminals to buy and sell stolen data and…
Earlier this month, Joseph Thacker’s neighbor mentioned to him that she’d preordered a couple of stuffed dinosaur toys for her…
Amazon Web Services (AWS) is pleased to announce a successful completion of the 2025 Cloud Computing Compliance Criteria Catalogue (C5)…
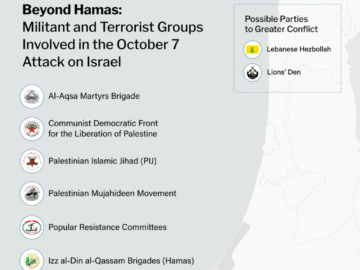
October 7: Hamas attacks Israel In the midst of the Israel-Hamas War, which erupted with a surprising and devastating attack…
When shadow IT is discussed, it’s usually in the context of unauthorized SaaS apps or stray cloud buckets. But there’s…
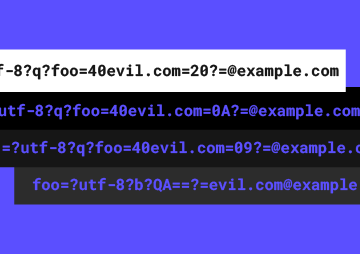
Threat actors are abusing the special-use “.arpa” domain and IPv6 reverse DNS in phishing campaigns that more easily evade…
Introduction In this post, we’ll show precisely how to chain round-trip attacks and namespace confusion to achieve unauthenticated admin access…