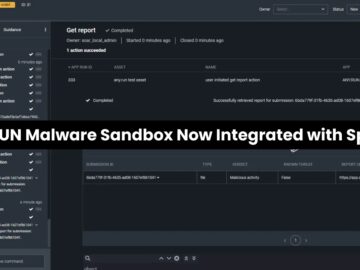
Splunk users can now leverage ANY.RUN’s sandbox and threat intelligence directly within their Splunk SOAR environment. This allows for the…
With Hezbollah and Lebanon still reeling from a coordinated wave of pager explosions on Tuesday that killed at least 12…
In a concerning development within the cybersecurity landscape, ransomware operators have adopted a novel approach to infiltrating networks by focusing…
Law enforcement agencies have successfully dismantled “Ghost,” a sophisticated encrypted communication platform allegedly designed exclusively for criminal use. The operation,…
A server misconfiguration exposed a trove of documents belonging to FleetPanda, a leading petroleum and fuel industry software provider. Sensitive…
A Chinese national has been indicted in the U.S. on charges of conducting a “multi-year” spear-phishing campaign to obtain unauthorized…
Research from Experian and TechUK has found less than a third of employees are aware their employer is using generative…
Block ciphers are a fundamental component of modern cryptography, crucial in securing data across various digital platforms. Unlike stream ciphers,…
Introduction: In an era where digital innovation advances rapidly and cyber threats evolve just as quickly, it is crucial for…
Firms in the construction industry are getting breached by hackers via internet-exposed servers running Foundation accounting software, Huntress researchers are…
Credential Flusher, understanding the threat and how to protect your login data Pierluigi Paganini September 18, 2024 Credential Flusher is…
Trojanized PDF readers are malicious software that are disguised as legitimate PDF viewing applications. They are primarily used by the…