Pen testing is an essential part of secure application development; it helps find vulnerabilities before they can be exploited, ensures…
[ This article was originally published here ] At (ISC)², we pride ourselves in our steadfast dedication to maintaining the…
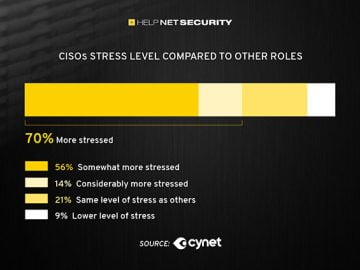
94% of CISOs report being stressed at work, with 65% admitting work-related stress issues are compromising their ability to protect…
Feb 23, 2023Ravie LakshmananSoftware Security / Supply Chain Attack Cybersecurity researchers are warning of “imposter packages” mimicking popular libraries available…
Damon Rees, the former chief executive of Service NSW, has been appointed to lead the review of the federal government’s…
A previously unknown threat actor named Hydrochasma has been targeting shipping and medical laboratories involved in COVID-19 vaccine development and treatments….
Microsoft has made it official that it is going to introduce the services of its AI ChatGPT on all its…
Amid uncertain economic conditions, the technology sector has been a hot topic of discussion in recent months due to the…
The Good Guys is the latest company to reveal that some of its customer leaked in a historical data breach…
Threat actors are targeting Internet-exposed Fortinet appliances with exploits targeting CVE-2022-39952, an unauthenticated file path manipulation vulnerability in the FortiNAC…
Several data center organizations were recently alerted by Resecurity regarding a malicious cyber campaign that has set its sights on…
Xcitium has unveiled its endpoint security solution, ZeroDwell Containment, for customers with or without legacy EDR products. Xcitium multi-patented technology…