Temu denies it was hacked or suffered a data breach after a threat actor claimed to be selling a stolen database…
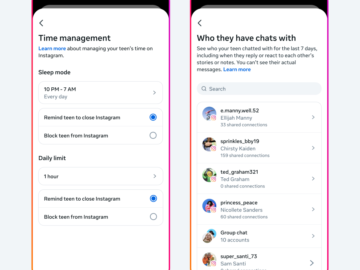
Instagram’s latest move to protect its younger audience takes shape with the introduction of “Teen Accounts.” Starting today, teens under…
Google will rework from scratch its plans to build a US$200 million ($296 million) data centre in Santiago after concerns…
Broadcom has fixed a critical VMware vCenter Server vulnerability that attackers can exploit to gain remote code execution on unpatched servers via…
When French prosecutors took aim at Telegram boss Pavel Durov, they had a trump card to wield – a tough…
Hackers are brute-forcing passwords for highly privileged accounts on exposed Foundation accounting servers, widely used in the construction industry, to…
Sky Betting and Gaming’s practices have come under scrutiny, resulting in a regulatory reprimand from the UK Information Commissioner’s Office….
Defence is looking for a cost-effective way to use Starlink to improve the quality of life of personnel serving on its roughly…
A rolling Cloudflare outage is impacting access to web sites worldwide, including BleepingComputer, with sites working in some regions and…
This pager runs on two AAA batteries, which, like any battery, could be induced to explode, but likely not with…
The Federal Communications Commission (FCC) has reached a $13 million settlement with AT&T to resolve a probe into whether the…
CISA and the FBI urged technology manufacturing companies to review their software and ensure that future releases are free of…