The person behind the bold SIM swap attack that led to the takeover of the U.S. Securities and Exchange Commission’s…
A 25-year-old Alabama man was arrested for hacking the US Securities and Exchange Commission’s X account earlier this year as…
An Alabama man was arrested today by the FBI for his suspected role in hacking the SEC’s X account to…
Radiant Capital was hit Wednesday by an apparent private key compromise that resulted in the loss of as much as…
North Korean IT professionals who trick Western companies into hiring them are stealing data from the organization’s network and asking…
A critical security flaw in SAP NetWeaver AS Java has been uncovered, potentially allowing attackers to upload malicious files and…
“Guilty until proven innocent,” writes Maxwell Alles in a Forbes article this week. That’s the way he likes to think of one…
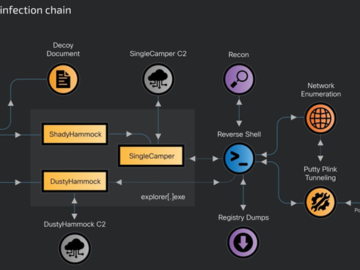
Oct 17, 2024Ravie LakshmananThreat Intelligence / Malware The Russian threat actor known as RomCom has been linked to a new…
The Metropolitan Police has taken over the investigation into allegations that a Post Office worker advised staff to destroy or…
Almost every week we add another workflow to our automation library. Our platform and copilot are helping people automate otherwise…
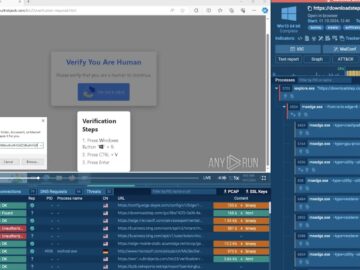
Lumma Stealer, also known as LummaC2, is a widely known malware that first surfaced in 2022. Since then, it has…
For the first time in the history of the tech industry, the U.S. Department of Justice (DOJ) has publicly acknowledged…